If you want to manually unblock the IP address 8
Fail2Ban is an application, Fail2Ban is an application / Linux / Fail2Ban is an application, Fail2Ban is an application (Fail2Ban is an application). Fail2Ban is an application, Fail2Ban is an application. Fail2Ban is an application.
Fail2Ban is an application (for example,. ssh, Fail2Ban is an application, Fail2Ban is an application, Fail2Ban is an application…), then blocks the attacker's IP address using iptables rules or by adding an entry to the /etc/hosts.deny file
then blocks the attacker's IP address using iptables rules or by adding an entry to the /etc/hosts.deny file:
1 | dnf install epel-release -y |
then blocks the attacker's IP address using iptables rules or by adding an entry to the /etc/hosts.deny file
1 | dnf install fail2ban fail2ban-firewalld -y |
then blocks the attacker's IP address using iptables rules or by adding an entry to the /etc/hosts.deny file:
1 | systemctl start fail2ban |
1 | systemctl enable fail2ban |
then blocks the attacker's IP address using iptables rules or by adding an entry to the /etc/hosts.deny file
then blocks the attacker's IP address using iptables rules or by adding an entry to the /etc/hosts.deny file. It's a good idea to make a copy of your main configuration file. It's a good idea to make a copy of your main configuration file:
1 | cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local |
It's a good idea to make a copy of your main configuration file. It's a good idea to make a copy of your main configuration file, It's a good idea to make a copy of your main configuration file:
1 | mv /etc/fail2ban/jail.d/00-firewalld.conf /etc/fail2ban/jail.d/00-firewalld.local |
It's a good idea to make a copy of your main configuration file, It's a good idea to make a copy of your main configuration file:
1 | systemctl restart fail2ban |
By default, Fail2Ban is not configured to block remote IP addresses. By default, Fail2Ban is not configured to block remote IP addresses, By default, Fail2Ban is not configured to block remote IP addresses.
By default, Fail2Ban is not configured to block remote IP addresses, By default, Fail2Ban is not configured to block remote IP addresses:
1 | nano /etc/fail2ban/jail.d/sshd.local |
Add the following lines:
1 2 3 4 5 | # Ta konfiguracja zablokuje zdalny host na 2 godziny po 3 nieudanych próbach logowania SSH. [sshd] enabled = true bantime = 2h maxretry = 3 |
By default, Fail2Ban is not configured to block remote IP addresses, and then restart the SSH service, It's a good idea to make a copy of your main configuration file:
1 | systemctl restart fail2ban |
and then restart the SSH service:
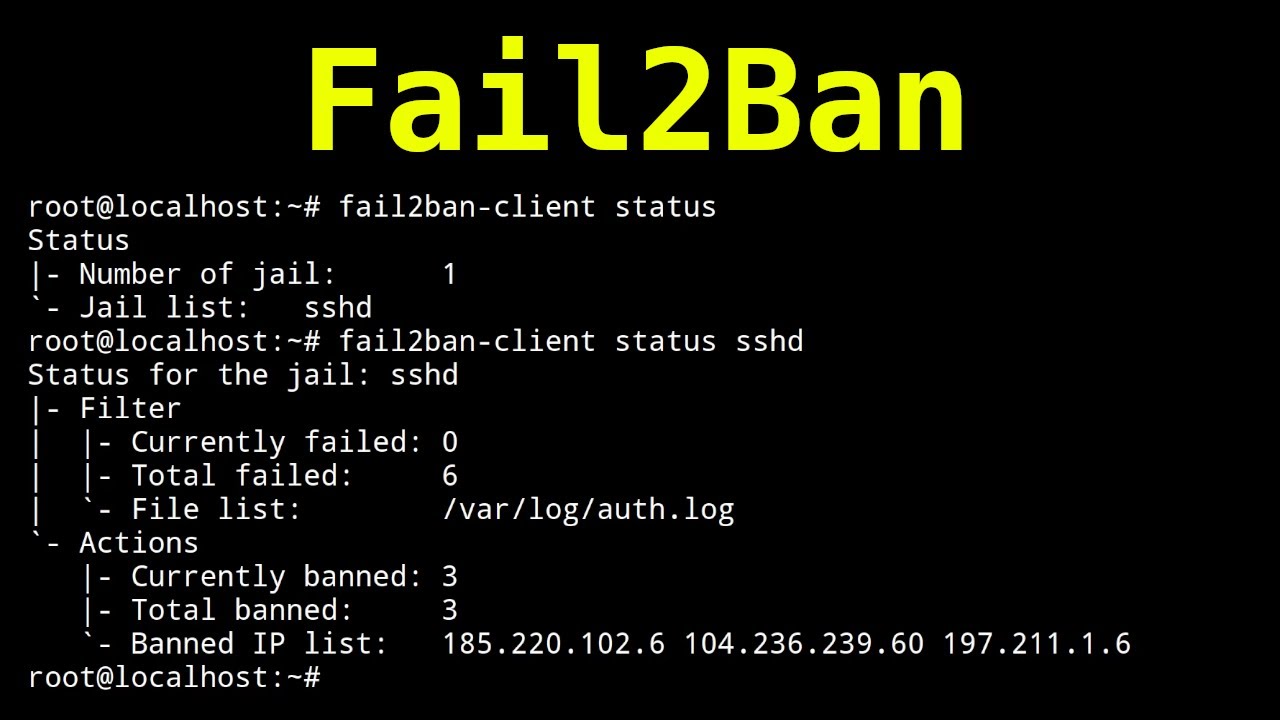
1 | fail2ban-client status |
and then restart the SSH service:
1 2 3 | Status |- Number of jail: 1 `- Jail list: sshd |
To check, and then restart the SSH service, It's a good idea to make a copy of your main configuration file:
1 | fail2ban-client status sshd |
and then restart the SSH service:
1 2 3 4 5 6 7 8 9 | Status for the jail: sshd |- Filter | |- Currently failed: 6 | |- Total failed: 15 | `- Journal matches: _SYSTEMD_UNIT=sshd.service + _COMM=sshd `- Actions |- Currently banned: 2 |- Total banned: 2 `- Banned IP list: 96.9.67.48 43.154.142.8 |
If you want to manually unblock the IP address, It's a good idea to make a copy of your main configuration file:
1 | fail2ban-client unban remote-ip-address |
If you want to manually unblock the IP address If you want to manually unblock the IP address